PERMISSIONS Administrator or Super Administrator privileges in Workplace
NAVIGATION Workplace Online > Team > Security > click ransomware incident
NOTE Ransomware detection is supported on Workplace Server and Workplace Desktop for Windows and Mac 7.4 or later, but we recommend that you use the most recent versions to enjoy the best possible user experience.
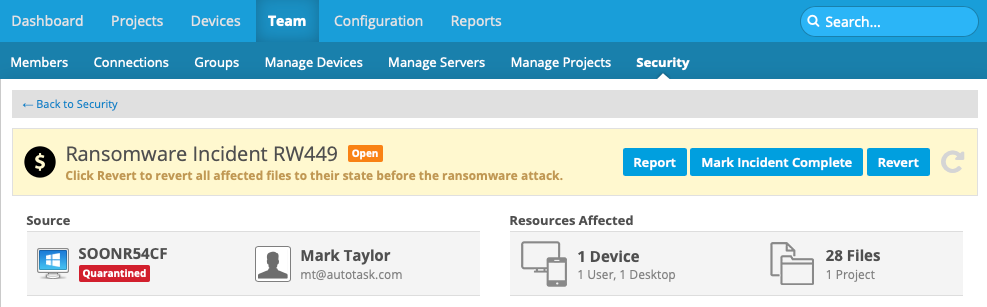
The Ransomware Incident detail page provides all the information and management tools you need to handle team security incidents detected by Workplace. Here, you can review incident details, confirm or ignore the incident, generate a report, track the incident through its lifecycle, revert affected files and export relevant information about them, review the status of affected devices, and drill to the Device Detail page for each device.
This page is comprised of four sections: Incident summary, Incident details, Revert Affected Files, and Affected Devices. Some sections will be expanded or collapsed by default, depending on the current status of the incident.
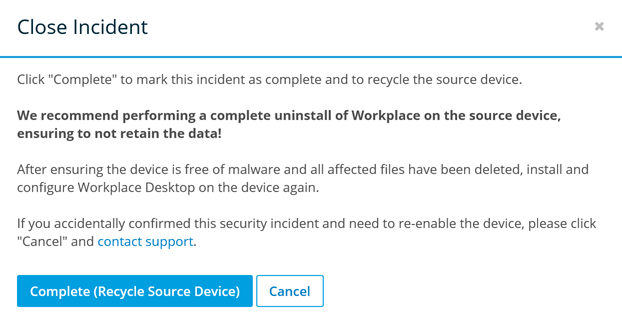
IMPORTANT This feature is designed to contain the security breach and to keep it from spreading via the sync process in the case of project files and, in the case of backup files, to provide a way to prevent backups of encrypted files and quickly revert backed up files to their last known good state. If you have a confirmed security incident, we recommend that you revert the affected files, recycle the device via Workplace, completely uninstall Workplace from the device (refer to Install or uninstall the Workplace app), scrub the device of all malware, reinstall Workplace, and restore the files from the service.
IMPORTANT The Workplace Ransomware Detection & Management feature alerts you of ransomware attacks on both your project files and your backed up files. As a result, you may see more than one incident for the same ransomware attack. We strongly recommend that you resolve ALL incidents through this interface to help ensure the security of your device and data.
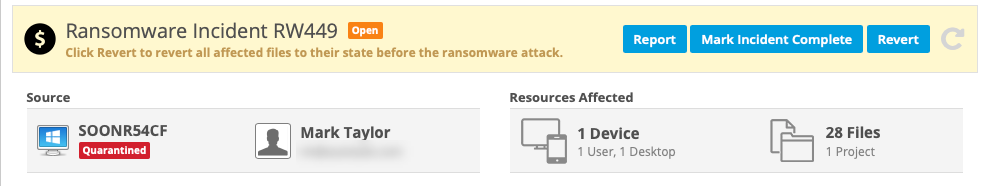
This section, located at the top of the page, displays the following general information about the incident:
| Area | Definition |
|---|---|
| Name and Status | Displays the name of the incident, which is comprised of the incident type and a unique system-generated alphanumeric code. Also displays the current status of the incident. Possible statuses are: New, Open, Ignored, and Completed. |
| Source | Displays the name of the device on which suspicious activity was detected, as well as the current device status. It also displays the name and email address of the device owner. Click anywhere in this area to open the Device Detail. |
| Resources Affected | This area displays the number of devices affected by the incident, including number of users and device types, as well as the number of files and projects affected by the incident. |
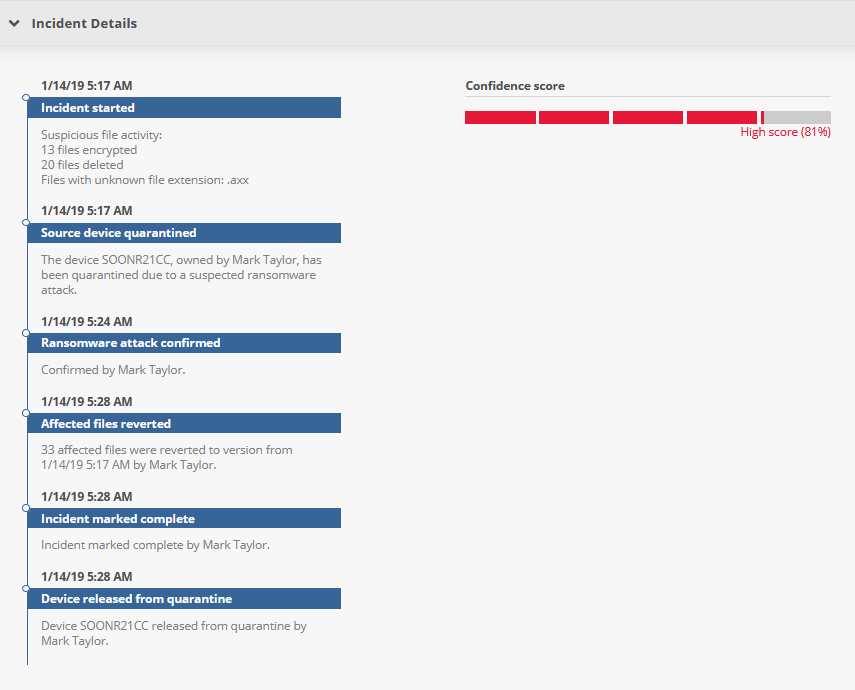
This section displays information about the reasons the incident was triggered, our confidence score on the validity of the incident, and a timeline summarizing incident handling. The areas displayed depend on the current status of the incident. All areas that can possibly be displayed are defined below:
| Heading | Definition |
|---|---|
| Incident Event Timeline | |
| Incident Started | The number of files affected and a description of the changes. |
| Source device quarantined | The name and owner of the device that has been quarantined due to a suspected ransomware attack. |
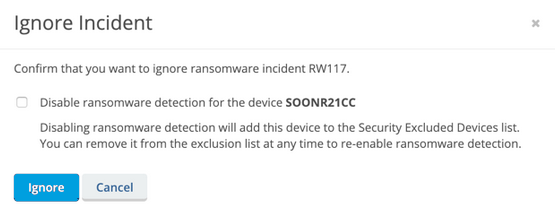
| Incident ignored | The name of the user who marked the incident Ignored. The name of the device added to the Security Excluded Devices list. |
| Device released from Quarantine | The name of the device released from quarantine and the name of the user who released it from quarantine. |
| Ransomware attack confirmed | The name of the user who confirmed the ransomware attack. |
| Affected files reverted | The number of files reverted, the name of the user who reverted them, and the version dates they were reverted to. |
| Incident marked complete | Name of the user who marked the incident Complete. |
| Device recycled | Name of the recycled device and the user who recycled it. |
| Confidence Score | |
| Confidence Score | This rating, calculated by the system, indicates the level of confidence we have that this incident is an actual security incident. |
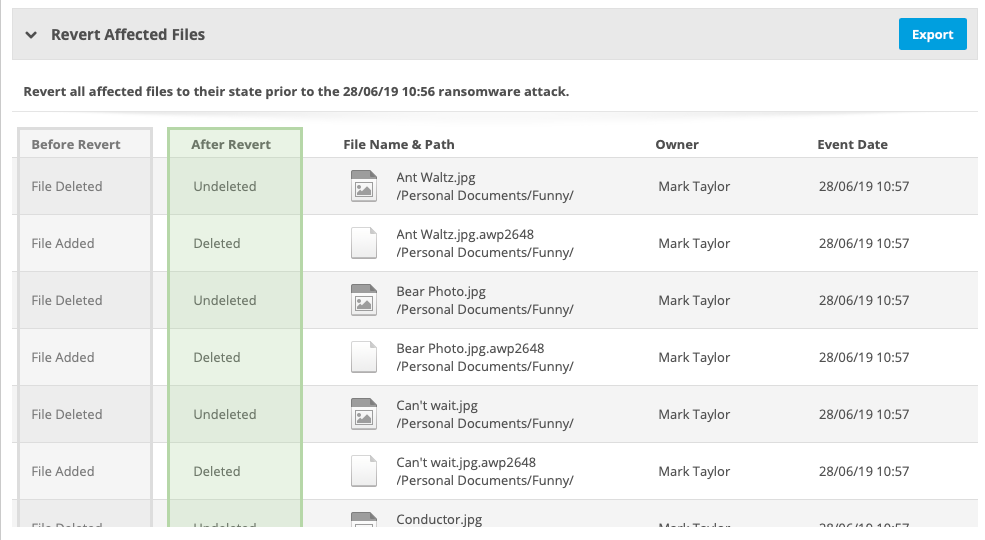
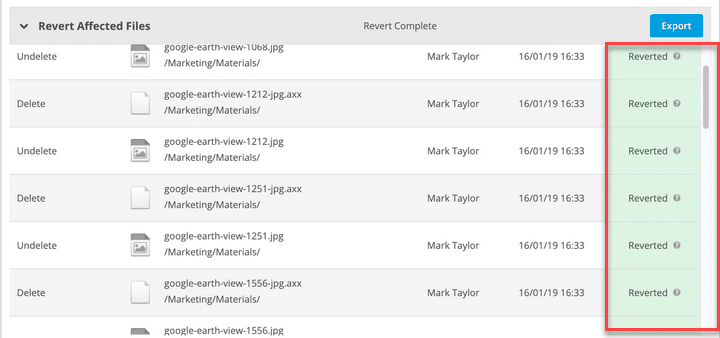
This section lists all the files affected by the ransomware incident and offers the opportunity to export the information or, when applicable, to revert the files to their state prior to the incident. The columns displayed depend on the current status of the incident. All columns that can possibly be displayed are defined below:
| Column | Definition |
|---|---|
| Before Revert | Describes the current state of the file. |
| After Revert | Describes the result of reverting the file to its state before the ransomware attack. |
| Revert Action | Describes the action executed by reverting the file. |
| File Name & Path | The name and path of the affected file. |
| Owner | The owner of the affected file. |
| Event Date | The date and time the change to the file was detected. |
| Reverted | The date and time the file was reverted. |
| Reverted By | The name of the user who executed the revert function. |
| Status | The reversion status of the file. The available statuses are Reverting and Reverted. If you are unsure of the status meaning, hover over the question mark icon to display a tooltip. |
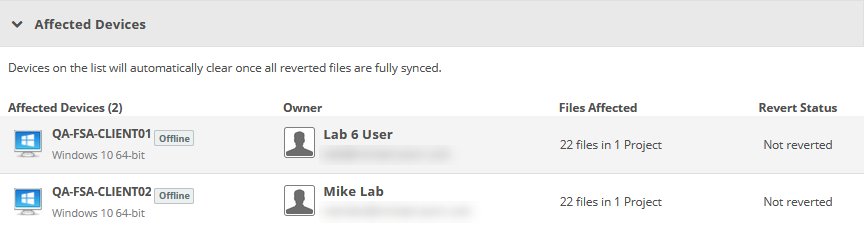
This section displays all devices affected by the incident. Click to open the Device Detail.
NOTE Devices on this grid will be cleared automatically when all reverted files are fully synced.
The following columns are displayed:
| Column | Definition |
|---|---|
| Affected Devices | The name, status, and operating system of the affected device. |
| Owner | The name and email address of the device owner. |
| Files Affected | The number of files and projects affected by the incident. |
| Revert Status | The revert status of the affected files on the device. The status may be either Not Reverted or Pending Revert. Once reverted files are synced, the device is removed from this grid. |
How to...
Click the Export button in the Revert Affected Files area.
NOTE You can only revert files for incidents with a status of Open.
TIP The Before Revert and After Revert columns indicate what the revert function will do.
NOTE You can only complete incidents with a status of Open.
- Click the Mark Incident Complete button.
NOTE If you complete an incident without first reverting files, the following popup window will be displayed. If you select Revert Files, you may monitor the revert process, then click the Mark Incident Complete button again.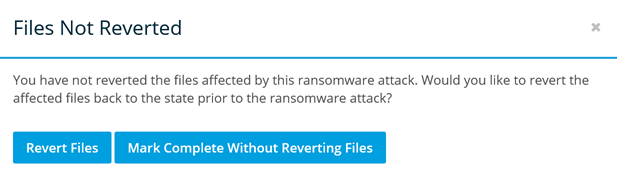
- Click Report.
- Proceed as your normally would from the resulting print dialog box.